- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ECP returning 403 Forbidden from AWS requests
We have a set of Roku devices in a LAB which we connected to our VPN and AWS.
In AWS we are running a CI tool which we want to use with the devices, and the devices are correctly responding to the CI host calls:
tmp-shel:~# nc -vz 100.101.250.39 8085
Connection to 100.101.250.39 8085 port [tcp/*] succeeded!
tmp-shel:~# nc -vz 100.101.250.39 8060
Connection to 100.101.250.39 8060 port [tcp/*] succeeded!
tmp-shel:~# nc -vz 100.101.250.39 80
Connection to 100.101.250.39 80 port [tcp/http] succeeded!
tmp-shel:~# telnet 100.101.250.39 8085
Connected to 100.101.250.39
However, when we attempt any request to the ECP, we receive 403, i.e:
tmp-shel:~# curl -vo /dev/null -s -w "%{http_code}\n" http://100.101.250.39:8060/query/device-info
* Trying 100.101.250.39:8060...
* Connected to 100.101.250.39 (100.101.250.39) port 8060 (#0)
> GET /query/device-info HTTP/1.1
> Host: 100.101.250.39:8060
> User-Agent: curl/8.0.1
> Accept: */*
>
< HTTP/1.1 403 Forbidden
< Server: Roku/12.0.0 UPnP/1.0 Roku/12.0.0
< Content-Length: 0
<
* Connection #0 to host 100.101.250.39 left intact
403
tmp-shel:~# curl http://100.101.250.39:8060/keypress/Home -X POST -d '' --verbose
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 100.101.250.39:8060...
* Connected to 100.101.250.39 (100.101.250.39) port 8060 (#0)
> POST /keypress/Home HTTP/1.1
> Host: 100.101.250.39:8060
> User-Agent: curl/8.0.1
> Accept: */*
> Content-Length: 0
> Content-Type: application/x-www-form-urlencoded
>
< HTTP/1.1 403 Forbidden
< Server: Roku/12.0.0 UPnP/1.0 Roku/12.0.0
< Content-Length: 0
<
* Connection #0 to host 100.101.250.39 left intact
The same actions work with no issue from our VPN:
➜ ~ curl http://100.101.250.39:8060/keypress/Home -X POST -d '' --verbose
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 100.101.250.39:8060...
* Connected to 100.101.250.39 (100.101.250.39) port 8060 (#0)
> POST /keypress/Home HTTP/1.1
> Host: 100.101.250.39:8060
> User-Agent: curl/7.87.0
> Accept: */*
> Content-Length: 0
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 202 Accepted
< Server: Roku/12.0.0 UPnP/1.0 Roku/12.0.0
< Content-Length: 0
<
* Connection #0 to host 100.101.250.39 left intact
➜ ~ curl -vo /dev/null -s -w "%{http_code}\n" http://100.101.250.39:8060/query/device-info
* Trying 100.101.250.39:8060...
* Connected to 100.101.250.39 (100.101.250.39) port 8060 (#0)
> GET /query/device-info HTTP/1.1
> Host: 100.101.250.39:8060
> User-Agent: curl/7.87.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: Roku/12.0.0 UPnP/1.0 Roku/12.0.0
< Content-Length: 3297
< Cache-Control: no-cache
< Content-Type: text/xml; charset="utf-8"
<
{ [1348 bytes data]
* Connection #0 to host 100.101.250.39 left intact
200
Per the similar post for 403 forbidden, this is usually fixed by using the device IP, but I am already doing it that way.
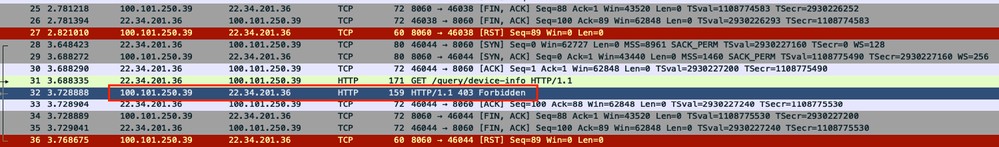
I have generated a tcpdump, and it shows the request made it to the Roku device, and then it rejected it.
Any insight would be appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ECP returning 403 Forbidden from AWS requests
On the device, go to Settings / System / Advanced system settings / Control by mobile apps. The default setting only allows ECP request from the private IP network addresses. If you set this to permissive, it will also allow requests across the device's subnet, which might work with AWS depending on how it's connected to your network. You might need some sort of local ECP proxy service running on your network to forward the requests from your AWS servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ECP returning 403 Forbidden from AWS requests
Thanks for your response.
- We enabled permissive in the devices and opened our firewalls for debugging, but the 403's keep coming. - We do see the TCP handshakes happening every time, but only when the http call to ECP is sent, it is rejected.
- We attempted the port 8085 but nothing is displayed at the time we send the requests.
We understand this could be because of the ECP security features rejecting those requests, but at the moment it is a black box why ECP decides to rejects them.
Do you happen to know if there is some documentation about those security features and maybe a way to further debug from the devices?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ECP returning 403 Forbidden from AWS requests
This is an intentional security feature to keep Roku devices from being controlled from the Internet. Since AWS's IPs are outside the subnet your devices are on, they get rejected by the server.
The only way to have this work is if you setup a proxy on your local network to which AWS can connect that would then forward the requests to the devices.